Sector 7G's Learning Center
Articles • Tips • Tutorials
Cyber Defense: Information and Parity
Intro
The following is an abridged version of Cyber Defense: Information Curation and Program Parity (Gregory Butler; September 2021), a separate work building upon Kill Chain Primer and Beyond The Kill Chain: MITRE’s ATT&CK, namely information acquisition as the necessary first tactical stage in cyber attacks.
What follows proposes that [1] vetted, curated, and valuable information is equally relevant defensively, and [2] cyber defense programs employing a flow of such information to leadership are better-positioned to achieve and maintain parity with other enterprise-critical divisions, a requirement that, most likely, may today be self-evident given threats’ impact, sophistication, and prevalence.
Defensive Information Acquisition
For this post’s content, only the first stage of the Cyber Kill Chain® is relevant: Offensive reconnaissance (target information acquisition). It logically follows that defense should engage in (continual) threat information acquisition, and it’s reasonable to assume that cyber programs, albeit to varying degrees, in fact do. Thus, consider the following, simple cyber defense program diagram centrally-positioning information acquisition:
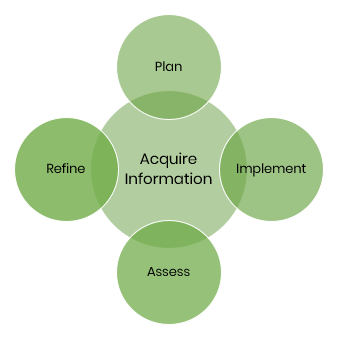
For this context’s purposes, only Acquire Information is relevant and the remainder beyond scope. Reiterating, the key is the diagram’s nucleus: acquiring (defensive) information. Thus, and tantamount to attacker reconnaissance, a cyber program’s effectiveness is necessarily bolstered by leveraging valuable information—ideally placing an attacker at an information disadvantage. But, valuable defensive information may be analogous to panning for gold and enterprises therefore may be deficient.
Acquisition of Valuable Knowledge
Acquisition of cyber defense information is nearly impossible to avoid. Headlined attacks and vulnerabilities, product and service pressure, feeds, inboxes, and myriad other sources are both the iceberg’s tip and the proverbial “firehose”.
Consequently, acquisition of valuable information, and to risk potential understatement, may be daunting. For example, information may be contradictory, redundant, speculative, employ unfamiliar terminology, or simply not be especially informative and therefore of little value (CrowdStrike alludes to this in their whitepaper Faster Response with CrowdStrike and MITRE ATT&CK, namely “In Desperate Need for a Common Framework” on page 3. Particularly compelling may be their examples of standardized nomenclature). However, while a common framework and language are certainly critical, by themselves they are not complete for information categorization, vetting, and curation, nor sufficiently valuable to influence meaningful action.
“Panning for Gold”
The graphic below presents cyber defense information intake, including vetting and curation, and categorizing both external (“Cyber Terrain”, i.e., the “firehose”) and organizational-level information (“Organization”). It’s not intended to in any way be instructional or comprehensive, only illustrative:
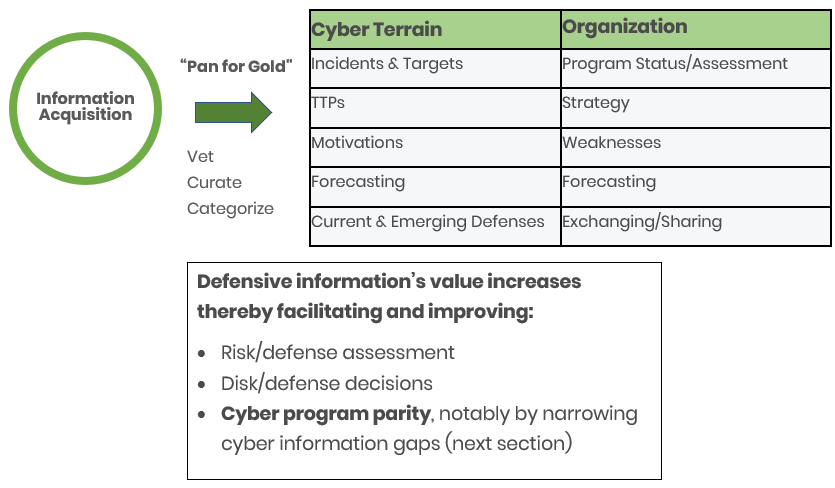
Cyber Program Parity
“Cyber program parity” refers to a state whereby an organization’s cybersecurity program operationally parallels other critical segments, like finance, sales, compliance, operations, etc. that are mature and thus accompanied by established processes ultimately flowing information to senior-most leadership. However, and at present, this may be the exception for cyber programs—for example, cyber program proliferation is relatively new, plus the subject matter remains fairly esoteric.
Information Gap
Until these and likely other factors adjust, although leadership is undeniably aware of cyber threats’ increasing risk, elevated concern cited by market research suggests information gaps and, therefore, potential lack of cyber program parity. Consider the following and how its content could change as defense information’s value increases (or decreases):
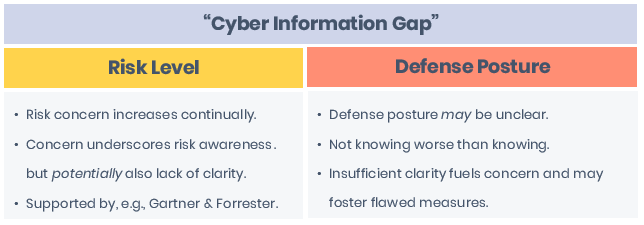
As a result, rationalizing bridging an information and parity gap may not be terribly difficult–after all, it’s just panning for gold…

Final Thoughts (Summary)
Parity Gap
- In best cases, organizations have mature, refined, and enforced cyber programs.
- Yet leadership concern understandably remains elevated. (See Sophos’ The State of Ransomware 2021, notably critical sector attacks where one may fairly presume defensive resilience.)
- Leadership may be unaware of or question program details. (Consider, for example, insurance reliance. One need not be a cyber practitioner to conclude that this is a flawed strategy; policy binders do not prevent loss.)
- Regardless, leadership may not be receiving vetted, curated, and, ultimately, reliable information.
Narrowing the Gap Must:
- Ensure cyber defense is in all aspects managed logically the same as any other business-critical segment.
- Regularly convey vetted, curated, and reliable information to leadership.
- Be integral to the complete cyber program.
- Measurably improve cyber optics and decisions and relieve concern to focus elsewhere.
